Time to acknowledge the facts on US-China cyber security
- By Dan Steinbock
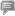 0 Comment(s)
0 Comment(s) Print
Print E-mail China.org.cn, July 11, 2014
E-mail China.org.cn, July 11, 2014
|
|
|
[By Jiao Haiyang/China.org.cn ] |
“State actors” and “black budgets”
In view of these historical legacies, the Justice Department’s “first-ever charges against a state actor for hacking” open the door to very different interpretations by its counterparts in China, which could replicate a tit-for-tat model for equivalent retaliation. In addition to China, such cases could be launched by other sovereigns that perceive themselves as targets of adverse cyber hacking originating from the U.S.
Historically, the Defense Department’s (DoD) military expenditures in the 1970s and ‘80s contributed to the nation’s technology boom and high growth rate in the 1990s. With the end of the Cold War, however, the wider U.S. intelligence community found itself in a new situation.
In the past, defense-related R&D fueled private-sector markets. During the technology boom in the 1990s, these roles were reversed. Today, it is private sector R&D that drives defense R&D – which is precisely why CIA invested in IQT, in order to stay close to the technology frontier and to leverage strengths from the global cyber marketplace.
It was only after the former NSA contractor Edward Snowden took his flight to Hong Kong over a year ago that observers have gotten a better idea of the reach of the U.S. intelligence community and its $52.6 billion “Black Budget.” These funds are in addition to the congressionally approved budgets of the Armed Forces and the Defense Department of $526.6 billion dollars. Reportedly, the NSA, the Central Intelligence Agency (CIA), and National Reconnaissance Office (NRO) receive nearly three-fifths of the black budget.
In the big picture, the story of the IQT is just a drop in the ocean. After all, its annual budget represents barely 0.1 percent of the “black budget”. Nevertheless, its leverage effect amounts to billions of dollars, according to IQT.
Ever since the privatization of the U.S. intelligence community, the rise of strategic venture capital and covert “black budgets,” the old boundaries have been blurred between the public and the private sector. In the process, the diffusion of innovations – including cyber security – has become faster and more global than any time before in human history.
In the civilian sector, that is a blessing because, as a public good, knowledge can contribute to wellbeing and growth. But in the security sector, it can be a curse because the spread of cyber weapons fuels strategic tension and potential for massive destruction.
The way out
In 2013, Washington and Beijing established a high-level working group on cyber security as a sub-dialogue of the two countries’ Strategic and Economic Dialogue (S&ED). These talks have been paralyzed for a year, after the stunning revelations of the whistleblower Edward Snowden.
In May, Washington indicted five PLA officers for alleged hacking of U.S. firms, which has contributed to further strategic distrust in Beijing. In June, the Obama Administration’s new cyberspace agenda was launched as a “multi-stakeholder approach to Internet governance.” From the Chinese standpoint, that approach remains predicated on U.S. norms, which differ significantly from those of large emerging nations.
Then, just days before the S&ED talks, the White House expressed its hope that cyber security talks could continue. While Beijing shares the goal, it does not find global mass surveillance or the Justice Department’s actions conducive to strategic trust.
There is a way out from the current bilateral strategic distrust. It is based on the acknowledgement of facts and sincere bilateral efforts to move on. That’s what the “new model of major power relations” is all about. Nobody said that it would be easy. But the alternatives are worse.
Dr. Dan Steinbock is Research Director of International Business at India China and America Institute (U.S.A.) and Visiting Fellow at Shanghai Institutes for International Studies (China) and the EU Center (Singapore). For more see: http://www.differencegroup.net
This article was first published at Chinausfocus.com To see the original version please visit http://www.chinausfocus.com/foreign-policy/time-to-acknowledge-the-facts-u-s-chinese-cyber-security-talks/





Go to Forum >>0 Comment(s)